Table of contents
Introduction
In the realm of modern web development, the ability to securely expose local services to the internet is paramount. Ngrok, a versatile tunneling software, has emerged as a favored solution for developers worldwide. In this comprehensive blog, we embark on a journey to unravel the intricate architecture of Ngrok. By delving into its inner workings, we aim to provide a deeper understanding of how Ngrok facilitates secure, seamless connections between local servers and external clients.
Understanding Ngrok's Architecture
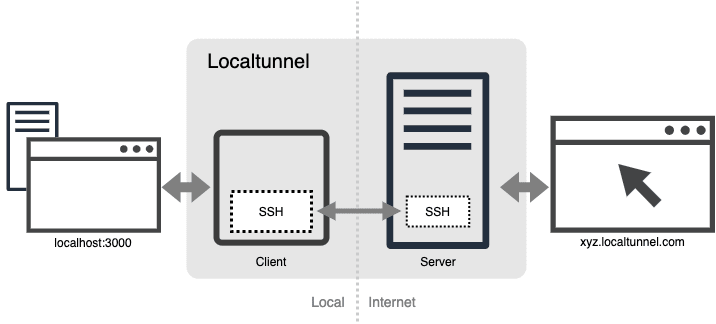
At its core, Ngrok operates on a client-server model, orchestrating the secure transmission of data between local machines and external networks. Let's dissect Ngrok's architecture into its fundamental components:
Client-side Component
The Ngrok client is installed on the user's local machine, serving as the interface for configuring and initiating tunneling sessions.
Upon invocation, the client establishes a secure connection with Ngrok's servers, acting as the conduit for data transmission.
The client encapsulates local traffic within secure tunnels, ensuring confidentiality and integrity during transit.
Ngrok Servers
Ngrok operates a fleet of servers distributed across geographically diverse locations to optimize performance and reliability.
These servers act as intermediaries between the client and external clients accessing the tunnel endpoints.
Ngrok servers employ robust encryption mechanisms to safeguard data in transit, mitigating security risks associated with exposing local services to the internet.
Tunnel Endpoints
Each tunnel established by Ngrok is assigned a unique URL or hostname, accessible from any device with internet connectivity.
Tunnel endpoints serve as the entry points for external clients seeking to interact with local services.
Ngrok dynamically manages tunnel endpoints, allowing users to create, modify, and terminate tunnels on-the-fly.
Security Layer
Security is paramount in Ngrok's architecture, with built-in mechanisms to protect against unauthorized access and malicious activities.
Data transmitted through Ngrok tunnels is encrypted using industry-standard protocols, safeguarding sensitive information from interception or tampering.
Ngrok offers authentication and access control features, empowering users to restrict tunnel access to authorized individuals or devices.
Exploring Ngrok's Inner Workings
To comprehend Ngrok's architecture in action, let's trace the journey of a request from an external client to a local server through a Ngrok tunnel:
Client Request
An external client initiates a request to access a local service exposed via Ngrok.
The request is directed to the Ngrok tunnel endpoint associated with the desired service.
Ngrok Server Processing
Ngrok servers receive the incoming request and route it to the corresponding Ngrok client instance.
The Ngrok client decrypts the request and forwards it to the local server through the established tunnel.
Local Server Response
The local server processes the incoming request and generates a response.
The response is relayed back to the Ngrok client through the tunnel.
Client Response
The Ngrok client encrypts the server response and transmits it back to the external client via Ngrok servers.
The external client receives the response and completes the interaction with the local service.
Ngrok's Beginner-Friendly Features
Simple Setup: Ngrok offers a straightforward installation process, making it accessible to users of all skill levels.
Intuitive Interface: The command-line interface (CLI) of Ngrok is user-friendly, with descriptive commands and helpful prompts.
Secure Connections: Ngrok prioritizes security, encrypting data transmission and providing authentication options for enhanced protection.
Versatility: Ngrok supports various protocols and services, enabling users to tunnel HTTP, TCP, and other types of traffic effortlessly.
Free Tier: For beginners and small-scale projects, Ngrok provides a free tier with limited features, allowing users to explore its capabilities without financial commitment.

Installing Ngrok on Linux
Follow these steps to install Ngrok on your Linux system:
Download Ngrok: Visit the Ngrok website (https://ngrok.com/) and navigate to the download section.
Select Linux: Choose the Linux version compatible with your system architecture (32-bit or 64-bit).
Extract the Archive: Once downloaded, extract the Ngrok archive to a directory of your choice.
Set Permissions: Navigate to the extracted directory and set executable permissions for the Ngrok binary:
chmod +x ngrokAuthentication: Sign up for a free Ngrok account to obtain your authentication token.
Authentication Setup: Run the following command and authenticate your account by providing the authentication token:
./ngrok authtoken YOUR_AUTH_TOKEN
Utilizing Ngrok: After installing Ngrok, you can start tunneling local services using the following command:
./ngrok <protocol> <port>
Replace <protocol> with the desired protocol (e.g., http, tcp) and <port> with the port number of the local service you want to expose.
Conclusion
As we conclude our exploration of Ngrok's architecture, we're left with a profound appreciation for its role in revolutionizing remote access and connectivity in the realm of web development. From its client-server model to the intricacies of tunnel endpoints and security mechanisms, Ngrok stands as a testament to innovation and ingenuity. As we continue to harness the power of Ngrok to streamline development workflows, showcase projects, and facilitate collaboration, let us embrace the endless possibilities it presents. Together, let's embark on a journey of exploration and innovation, empowered by the seamless connectivity and security that Ngrok affords.
Twitter: https://twitter.com/IngoleNehal
Hashnode: https://hashnode.com/@Nehal71

